HIPAA law goes by many names:
- The HIPAA Security Rule
- The HIPAA Privacy Rule
- “HIPPAA” Law
- HIPAA Confidentiality Law
- PHI Data Protection Law
- Private Patient Information Law
They’re all facets of the same thing (and one misspelling).
By any name, HIPAA contains hundreds of opportunities for employers to fall prey to millions in fines.
There are a thousand doors for protected information to sneak through, and tech is always rapidly advancing, creating more. But should you worry more about breaches from networks, physical IT, or some other source?
This article will show you the biggest HIPAA law pitfalls, based on an analysis of recent fines and breaches.
What is HIPAA Law?
What’s the definition of HIPAA law?
The full name is the Health Insurance Portability and Accountability Act.
The definition of HIPAA is: The US data privacy and data security law that safeguards Protected Health Information (PHI).
It’s basically the law that protects patient info from falling into the wrong hands. It puts the burden of protecting PHI on the provider.
HIPAA Privacy Rule vs Security Rule
The HIPAA Privacy Rule is the law that protects patient PHI from leaks. It establishes national standards that shield patient medical records and other protected health information.
The HIPAA Privacy Rule applies to health care providers, clearinghouses, and plans.
The HIPAA Security Rule is a more narrow subset of the Privacy Rule. It specifically protects electronic health information.
How Do Employers Run Afoul of HIPAA Law?
Private clinics and practices can get hit with the same HIPAA law problems as massive healthcare providers.
In a MedPro survey of HIPAA violations, we found that lack of regular Risk Assessments and Risk Management Plans caused the most common and costly fines.
Other major culprits include failure to protect PHI, either in physical equipment like laptops and USB drives, or in networks.
For the full list of major HIPAA Security Rule and Privacy Rule pitfalls, see below. (Click to download as a PDF.)
Click to download these common HIPAA law pitfalls as a PDF.
What is HIPAA PHI?
PHI is “Protected Health Information.”
Any release of it to third parties by “covered entities” violates HIPAA law’s Privacy Rule.
Examples of PHI include:
- Patient billing info
- Appointment scheduling notes for patients
- Patient emails about medications
- Blood test results
- MRI scans
- Phone records
Examples of non-PHI health info include:
- Calories burned
- Steps in your pedometer
- Heart rate readings without info that identifies the patient
- Blood sugar readings without info that identifies the patient
What is a HIPAA “Covered Entity?”
Covered Entities are those that provide treatment, operations, or payment in healthcare. All covered entities are subject to HIPAA law.
Covered entities include:
- Doctors’ offices, clinics, dental offices, psychologist offices
- HMOs, insurance companies, health plans
- Nursing homes, healthcare agencies, hospitals
- Health clearinghouses, government healthcare programs
- Pharmacies
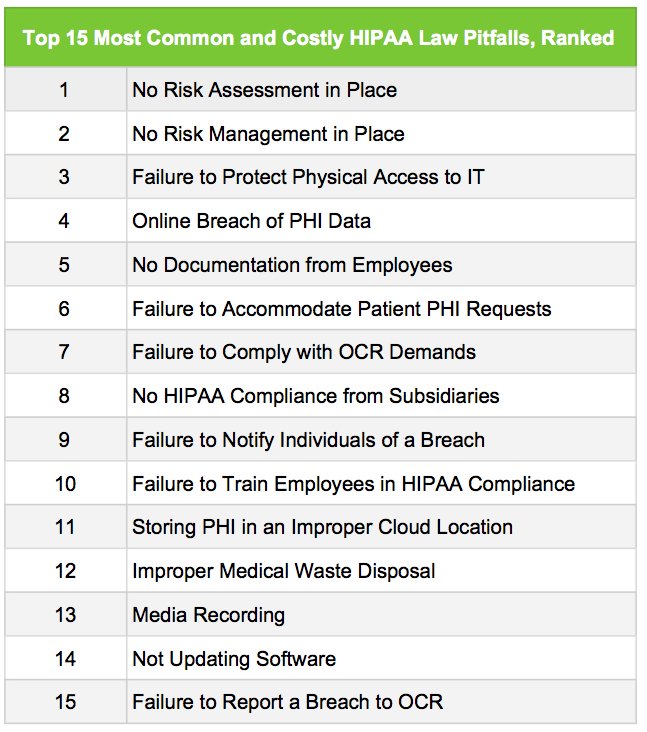
15 Big HIPAA Law Pitfalls to Run from Like Godzilla, Ranked
What is HIPAA’s biggest, meanest violation?
The list below contains the biggest HIPAA law pitfalls of 2016 and 2017. We’ve ranked them in order of most common and costly.
The rankings come from a MedPro analysis of 2016 and 2017 HIPAA violations. Each has resulted in fines of over $1 million for individual providers.
1. Failure to Conduct a Regular HIPAA Law Risk Assessment
Here’s a horror story.
Your office admin hands you a sheet of paper.
It’s a letter from OCR. You’re being investigated for a HIPAA law breach.
That’s bad enough, but when the ashes settle, you get a second fine because you didn’t conduct a regular HIPAA Risk Assessment.
That infraction boosts your penalty into the seven-figure zone.
This scenario has played out nightmarishly for several healthcare employers in 2016 and 2017.
This is the most frequent and most costly HIPAA violation.
Why is it so prevalent? Because it piggybacks on other HIPAA Privacy Rule breaches.
Example HIPAA Law Breach
In 2016, a healthcare employee left a company laptop in his car. When a thief stole the laptop, PHI was compromised.
The fine? $5.55 million.
A big part of that came from failure to conduct a risk assessments.
So, just what is a HIPAA risk assessment?
A HIPAA Law Risk Assessment is required by DHHS for all covered employers that handle PHI.
A Risk Assessment Is an Internal Analysis that Covers:
- Any risks to PHI data, including electronic media, transmissions, portable media, networks, desktops, business associates, etc.
- Data storage, including hosting providers.
- Potential vulnerabilities and threats.
- Determining the likelihood of threats.
- Determining the likely impact of threats.
- Assessment of current security measures.
- Determining your overall risk level, with corrective actions planned.
- Retaining final analysis in writing in case of a HIPAA law investigation.
How Often Should You Conduct a HIPAA Risk Assessment?
The HIPAA Security Rule doesn’t mandate a timeline for risk assessments. That said, providers should at least reassess HIPAA violation risk every time they plan to adopt a new technology.
You should also reassess risk when changing business operations.
Given the pace of technology and business, once a year is probably the best window. Every six months is not unreasonable.
The HIPAA Law Breach: Laptop stolen, PHI data compromised, upon investigation, OCR found no risk assessments were conducted.
The Fix: Conduct regular risk assessments and document them to avoid an ugly HIPAA Privacy Rule violation.
Bonus Violation: A MedPro analysis found several 2016 HIPAA law breaches where the lack of risk assessments added insult to injury. Fines reached the tens of millions.
Find Out How Much You Can Save Instantly.
Try our on-line savings calculator.
2. Failure to Enact a HIPAA Law Risk Management Plan
Along with regular risk assessments, healthcare providers should adopt a Risk Management Plan.
This is the second most common and costly HIPAA law risk.
Example HIPAA Law Risk Management Plan Violation:
In a 2016 HIPAA Privacy Rule violation, an employer was fined $4.8 million when PHI data was left open to internet search.
Exacerbating the fine/violation was the lack of an adequate Risk Management Plan.
So what is a HIPAA Risk Management Plan?
A Risk Management plan is a document that outlines activities. The activities attempt to identify and minimize the risks of a HIPAA confidentiality breach.
The plan is only as good as its implementation. Employers should deploy the plan through training, procedures, enforcement, and documentation.
The HIPAA Law Breach: Compromised PHI data due to accidental online sharing. Missing/inadequate risk management plan.
The Fix: Build a risk management plan, and update it with regular risk assessment. To download a sample plan from HHS, click the image below.
Click to download the full HHS HIPAA Risk Management plan as a PDF.
3. Not Protecting Physical Access to PHI Data
Your car window has been smashed.
You realize with spreading horror that you left an unencrypted laptop in the car.
You’ve compromised PHI data. You’ve violated the HIPAA Security Rule.
After an OCR investigation, your practice is fined millions.
What did you do wrong?
The HIPAA Privacy Act charges you with protecting patient data. Leaving it in a car, on an unencrypted laptop, doesn’t count.
This is an actual scenario from 2016.
Failure to protect physical access to IT or PHI is the third biggest source of HIPAA law violations.
Laptops, USB drives, and external hard drives can contain PHI. Even smartphones or printer buffers can fall under HIPAA confidentiality rules.
Basically, any device that can contain data should be part of your risk management and assessment.
The HIPAA Law Breach: Stolen laptop containing PHI data. Laptop unencrypted. Employee didn’t protect physical IT.
The Fix: Include all possible physical IT in Risk Management plan and regular Risk Assessment. Create policies to protect devices that can contain PHI.
4. Failure to Protect Internet Access to PHI Data
Here’s the fourth most common and costly HIPAA law violation:
Failure to protect online access to PHI.
This should be a no-brainer. Unfortunately, the internet is something like an old-style set of Christmas tree lights: One goes out, they all go out.
Or, more accurately, one hole leaks PHI data, and we run afoul of the HIPAA Security Rule.
There are dozens of cases of sensitive patient data finding egress through the web. In one, a doctor tried to shut down a personal computer, but he accidentally left PHI open to the internet.
The fine? Nearly $5,000,000 for this HIPAA Privacy Rule breach.
The only way to plug the internet hole is to enact a robust and vigilant IT security plan. Our networks and storage should be evaluated regularly. How often?
Healthcare IT systems that store PHI should be risk-assessed at least yearly. Every six months is not unwarranted.
Further, the system should be reassessed whenever anything is about to change. That could mean installing software, updating software, installing equipment, or adding a new line of business.
The HIPAA Law Breach: PHI data left open to the internet.
The Fix: Regular Risk Assessment and a Risk Management plan that scrutinizes IT, data storage, and networks for possible leaks.
5. Not Getting PHI Data Protection in Writing
In one HIPAA law case, a stolen laptop led to more than just failure to protect PHI on physical IT.
An OCR investigation also found another HIPAA Security Rule breach. Namely, the employee who lost the laptop never signed documentation assuming responsibility for PHI.
This can lead to a case where the employer says, “We trained that employee in HIPAA compliance.”
Meanwhile, the employee says, “Yes, but no one told me locking a laptop in my car wasn’t enough protection.”
In order to be safe from HIPAA security rule breaches, the healthcare provider should create signed documentation.
The document could have outlined all responsibilities of the employee, including proper use and storage of laptops, USB drives, smartphones, and the like.
The HIPAA Law Breach: Stolen laptop, with no documentation signed by the employee and outlining proper physical protection of IT.
The Fix: Use a Risk Assessment and Risk Management plan to detail proper use and storage of physical IT that can carry PHI. Have all employees sign off on the plan.
6. Not Complying with Patient Requests for PHI Data
It’s mystifying.
Actually trying to comply with HIPAA law can make us break it.
That’s what happened in the case below.
In a 2016 HIPAA privacy rule violation, a medical practice refused to send records to over 40 patients on request.
According to the HIPAA Privacy Act, healthcare providers must comply with patient requests to release medical records within 30 days.
The way around it? Put policies in place to release patient medical records. Rather than fearing HIPAA law, learn to work within it.
The HIPAA Law Breach: Refusal to release patient PHI data on request.
The Fix: Train employees in HIPAA compliance. Enact a policy for how to release patient data safely.
7. Failure to Comply with OCR HIPAA Law Requests
This one ought to be a no-brainer.
Even so, it’s common and costly enough to be our #7 HIPAA pitfall.
After violating HIPAA law, a provider allegedly refused to comply with or respond to OCR’s demands to rectify the situation.
In other words, if OCR steps in and tells you to correct a privacy rule conflict, do as they request.
The HIPAA Law Breach: Failure to respond to OCR requests to fix a previous HIPAA Privacy Rule violation.
The Fix: Comply promptly with all OCR requests.
8. Not Ensuring HIPAA Law Compliance from Subsidiaries
It’s possible to be compliant, yet still run afoul of HIPAA law.
In this example, a healthcare employer’s subsidiaries were found non-compliant.
The violations? There were several, arising from different areas of the Privacy Act.
The point? It’s the parent company’s responsibility to make sure subsidiaries are compliant. Employees at those companies also need compliance training.
The fine in this case? $4.3 million.
The HIPAA Law Breach: Non-compliant subsidiary companies.
The Fix: Make sure every organization and employee you’re responsible for receives proper training and assessment.
9. Failure to Notify Individuals of a HIPAA Privacy Rule Breach
In yet another missing laptop case, PHI for 10,000 patients vanished. This time, the fine was $2.7 million.
The provider failed to notify each of the 10,000 individuals that their PHI was compromised.
A HIPAA law entanglement can be a devastating event. However, when it happens, dealing with it properly is critical.
Just like we plan a response to fires or other emergencies, we also need to plan for HIPAA confidentiality breaches.
The HIPAA Law Breach: Not notifying victims of a breach.
The Fix: Have a plan for how to deal with PHI data slipups.
10. Botched HIPAA Law Employee Training
Here’s another HIPAA law horror story.
You learn you’re being investigated by OCR. Why?
Some of your employees stored PHI data in a Google sheet.
This real-world case resulted in a fine of $2.7 million.
The cause? Inadequate employee HIPAA compliance training.
Had those employees received proper instruction, they’d have known that unsecured cloud-based storage systems are no place for PHI.
An adequate Risk Management plan would specify where and how to store PHI. It also would have had employees sign off on their responsibility.
The HIPAA Law Breach: Improperly trained employees stored PHI data in an unsecured Google doc.
The Fix: Train employees in HIPAA compliance, including where and how to store patient data. Have employees sign off that they understand their responsibility.
11. Storing PHI in an Improper Cloud Location
In the example above, employees (including physicians in training) stored PHI data in Google docs available online.
We used the example to illustrate poor employee training. However, it outlines another HIPAA law pitfall.
Namely, improper cloud-storage locations for PHI.
Google Docs (also known as G Suite) can be used as HIPAA compliant PHI data storage locations.
However, it takes a little wrangling. Being safe with Google docs for instance requires Google administrators to sign a BAA with the provider.
The HIPAA Law Breach: Storing PHI data in an unsecured Google doc.
The Fix: Store PHI only in approved, secure locations to avoid a HIPAA Privacy Rule violation.
12. Improper Medical Waste Disposal of Materials Containing PHI Data
PHI data is like infectious material. It’s always trying to get out, and it finds ways you’d never dream of.
Until, that is, you run into a HIPAA law pitfall that destroys your practice.
In a $2.25 million HIPAA privacy rule breach, a Rhode Island pharmacy was fined for improper medical waste disposal.
How can medical waste break HIPAA confidentiality?
In this case, the pharmacy was tossing out unused pill bottles, or bottles with typos on the labels.
The bottles contained sensitive PHI data, like patient names and addresses.
The HIPAA Law Breach: Patient info on unused pill bottles thrown in the trash.
The Fix: Ensure employee HIPAA law compliance training. Have a Risk Management Plan, and update it through regular Risk Assessments.
Bonus Violation: In a related HIPAA law breach, a private practice was fined for (admirably) recycling X-Ray films. Unfortunately, those films contained PHI data.
13. Media and Recording Breaches of the HIPAA Privacy Rule
Picture this:
You agree to let a camera crew shoot B-roll in your practice. A few weeks later, HIPAA law violation.
This actually happened to a hospital in 2016. The fine in this case? $2.2 million.
Did the camera crew actually record PHI? That didn’t matter to the court. What mattered was, they could have.
Now, maybe you won’t be letting any reality TV show crews into your clinic.
But consider this: with the proliferation of smartphones, can you really guarantee that you’re protecting all PHI?
What if a patient films a smartphone video and puts it on Facebook? In the background, you can see or hear another patient talking.
While we haven’t found evidence of an iPhone video HIPAA violation, anyone who thinks it isn’t coming isn’t thinking hard enough.
The HIPAA Law Breach: Video equipment in healthcare facility.
The Fix: Include camera and smartphone policies in Risk Management plan. Make sure all PHI is protected at all times from accidental viewing.
14. Failure to Update Software and IT Systems
You’ve got a locked-down IT system. Nothing’s getting out.
Then it crashes.
Unfortunately, the new server’s default settings are left on. PHI data is open to the public. Suddenly you’re in violation of HIPAA law.
Unfortunately, this real-world breach cost a healthcare facility $2.14 million.
Providers should plan for emergencies. They should also reassess their risk before they make IT changes.
The HIPAA Law Breach: PHI left open to the internet because of failure to change default settings on a brand new server.
The Fix: Risk Management plans should provide policies for making big changes to the IT system, including those resulting from emergencies.
15. Failure to Report a HIPAA Law Breach to OCR
The HIPAA law pitfalls above are enough to give a doctor night sweats.
Compounding them is what we do when we trip up.
Imagine this:
You get investigated by OCR. You’re found guilty. Why?
An employee went home with a thumb drive seven months ago. On it, she’d stored patient records.
Though this scenario is real (and cost the provider millions) here’s an added headache:
Your fine doubles because you didn’t report the breach within a reasonable amount of time.
Covered entities must notify all breaches of PHI to HHS. If the breach concerns less than 500 people, you have 60 days.
If the HIPAA Privacy Rule violation affects more than 500 people, the window shrinks to “without unreasonable delay.”
Fessing up is the best way to keep a damaging wreck from turning catastrophic.
The HIPAA Law Breach: Failure to report a PHI breach to HHS.
The Fix: Add a policy to your Risk Management plan for rapid reporting of all HIPAA breaches.
Conclusion
HIPAA law provides staggering penalties for those who violate its security and privacy rules
Fortunately, most violations can be curtailed through adequate employee training, employee documentation (signing off), regular Risk Assessment, and a written, living Risk Management plan.
The biggest HIPAA law pitfalls involve not performing Risk Assessments, not having a Risk Management plan, and PHI data breaches from unprotected physical tech and open networks.
It’s vital to remain vigilant to lightning-fast changes in technology in order to stay clear of violations of the HIPAA Privacy Rule.
Got a HIPAA law comment or suggestion? (Or “HIPPAA” as some call it?) Give us a shout in the comments below!